With hundreds of cyber-security brands out there, cutting through the noise is harder than ever.
As b2b cyber-security marketing and PR specialists, we’re well-versed in ensuring brands get noticed. In this 101 guide, we answer the cyber-security PR and marketing questions we get asked most frequently (like, all the time) by clients and prospects.
Your cyber-security marketing questions answered
Q: A lot of our work is highly sensitive. If we can’t talk about specifics, is there any point in investing in PR or marketing?
A: Why having shy customers doesn’t have to hinder your cyber-security marketing strategy
Q: How can we ensure our messaging resonates with non-technical budget-holders and decision-makers?
A: Your cyber-security brand needs to learn how to talk to non-technical people – here’s how
Q: Do we need spokespeople? If so, who should we pick – and how do we prepare them to speak to the media?
A: Cyber-security marketing: Building out a spokesperson bench
Q: Do cyber-security brands need to maintain a serious tone of voice?
A: Do cyber-security brands need to maintain a serious tone of voice?
Q: Why are our competitors getting more coverage than us at trade shows and conferences?
A: Landing a media briefing at cyber-security trade shows like Black Hat
TL;DR? Watch our cyber-security marketing and PR top tips
Why having shy customers doesn’t have to hinder your cyber-security marketing strategy
As we all know, the trusty customer case study is an important component of any PR or marketing campaign – no matter what the industry.
Case studies help businesses demonstrate how their product or service has been successfully implemented by customers. They provide an excellent proof point for a product’s value in a certain sector, and highlight how it can be used to address a specific business issue.
Instead of just talking about a product in theoretical terms, case studies allow brands to showcase practical applications. Most importantly, they help bring a (highly technical) product to life by letting brands tell stories that are much more engaging than yet another self-serving press release.
However, finding customers willing to be used as case studies is notoriously difficult in the cyber-security space, primarily due to the sensitive nature of the topic. So, how can brands use customers in their cyber-security marketing and PR strategies without placing them under the spotlight? Here are a few options.
Use their data, not their name
Virtually all modern cyber-security products collect a huge amount of data from the analysis of things like network traffic, device performance and employee activity. So, even if you can’t use a customer’s brand name, you might be able to use their data (with their permission, of course) to talk about what’s happening in the industry, or point to trends that align with your marketing messaging.
For example, a customer might have suffered a rare type of attack, or a variation of an existing threat that hasn’t been seen before. Or, multiple customers operating in the same industry might have suffered a similar attack within a short timeframe, suggesting that a specific type of company is being targeted.
This is all interesting data that could be used as part of a PR campaign addressing the wider threat landscape (think press briefings and speaking slots), or simply as a one-off piece of content like a blog or press release to showcase your expertise.
And the best part is that it can all be anonymized, so the customer in question doesn’t have to worry about its name appearing across cyber-security publications, blogs and social media feeds.
Make the most of awards season
Another extremely effective way of showcasing and validating all the great work you’ve done with customers without publicly naming them is to enter into industry awards.
With competition in the sector continuing to intensify, industry awards provide a valuable opportunity to illustrate your cyber-security brand’s expertise. They also help to build credibility and authority, providing third-party endorsements that add weight to any PR or marketing strategy.
Winning (or even just being nominated for) an award from a respected industry body proves that your product really is as good as you say it is, which builds trust with both current and potential customers.
Most importantly, the finer details of the entry and the work you’ve completed with a customer can be kept private, so that they are only read by the judging panel. This enables customers to be used as part of your cyber-security marketing strategy, even if they are concerned about revealing business secrets to media.
Plus, who doesn’t enjoy a glass of prosecco and the inevitable shrimp cocktail that comes with attending an awards evening?
Get persuasive
Finally, it’s always worth trying to convince any reluctant customers about the benefits of taking part in a case study. Just remember to keep the following tips in mind:
- Start off by targeting your happiest customers – i.e. those that you think will be the most likely to agree and that have previously been open to sharing their experiences of using your product or service.
- Highlight the mutual benefits – a case study doesn’t just have to benefit you, it can also be of value to the customer. For example, customer benefits could include increased visibility and the opportunity to show how they are now better able to serve their own customers.
- Offer incentives – when signing the client, why not offer a price reduction if they agree to provide a written or video case study about their experiences? Although you’ll have to make an initial sacrifice, this strategy could yield a greater financial return in the long run.
- Make the process as simple as possible – the less time and effort a customer has to put into writing and approving the case study, the more likely they will agree to it. Plan the process efficiently and don’t take up too much of their time.
Ultimately, it will always be tricky for cyber-security brands to find customers that are willing to be used as case studies. Cyber-security is a sensitive area, so many companies are understandably reluctant to talk about their experiences openly.
But, by thinking about how customer stories can be used in different ways – such as in award entries or through anonymized data – cyber-security brands can bolster their marketing strategies and get even more value out of their customer relationships.
Struggling to make the most of your customer references? We can help. Get in touch at hello@rlyl.com.
Your cyber-security brand needs to learn how to talk to non-technical people – here’s how
The cyber-security landscape is filled with enough buzzwords and acronyms to make your head spin. And that’s before you delve into the highly technical nature of many solutions.
When communicating externally, cyber-security brands often fall into the trap of alienating their audience by elaborating on the minutiae of their product or using too much jargon. Brands need to remember that decision-makers and budget-holders often aren’t as cyber literate as they are.
Here are some top tips to ensure your cyber-security PR and marketing is impactful – and resonates with both technical and non-technical people.
Keep it simple, stupid
You might have heard that the internet is physically changing our brains, making our attention spans shorter and our memory worse. In the digital age, we’re constantly bombarded with competing messaging from brands – and we forget 99% of what we see.
To ensure your messaging captures the attention of your audience, make sure you:
- Use images and infographics to make technical concepts easier to digest.
- Employ analogies to explain complex topics.
- Make video part of your day-to-day – for social media, try to keep it under 90 seconds.
- Break up content – Twitter threads, video series, and listicles are all great techniques for breaking up content into digestible chunks.
- Avoid unnecessary acronyms, jargon, and technical language – using these won’t make your audience think you’re smart. Instead, you’ll lose their attention.
- Back up your points with real-world examples.
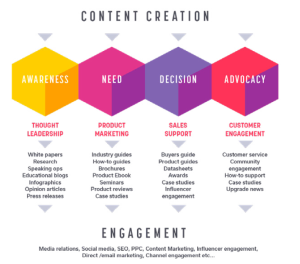
There’s a huge range of content cyber-security brands can (and should) be using.
Tailor your messaging to different levels of cyber literacy
Most cyber-security brands are adept at talking to CISOs, CIOs, and even CTOs. But what about the panicked CEO whose business has just been hacked? The CFO responsible for allocating spend to cyber-security? A journalist doing research for an article?
All these people will have different levels of understanding. And if your messaging goes over their head, they’re likely to click away from your content and head to a competitor.
A good way to avoid this is to split your content into different streams. One centered on the business case, another that’s technically focused, and a third that’s more generally educational or thought leadership based.
After all, why should people take your advice or buy your product if they can’t understand what you’re saying?
Need to develop jargon-free messaging for your cyber-security brand? We can help. Get in touch at hello@rlyl.com.
Cyber-security marketing: Building out a spokesperson bench
By Joel Khalili
For cyber-security brands, breadth and depth are equally important when it comes to building out a spokesperson matrix.
As the public faces of the company, spokespeople are central to defining a brand’s voice and public perception. For this reason, selecting precisely who to put in front of the press is a decision well worth taking time over.
Building out a spokesperson matrix is all about balance – between technical and non-technical expertise, too many voices and too few, individuals with passion, and those with poise.
It’s also important to assess each opportunity as it comes, and ensure the best equipped and most suitable spokesperson is selected.
With all this in mind, here are a few key considerations for any cyber-security brand looking to build an industry-leading spokesperson line-up.
Variety is the spice of life
For many cyber-security marketers, it can be tempting to lean on a single individual for all media opportunities. Start-ups and scale-ups in particular tend to rely on the founder or CEO to fly the flag for the company.
This inclination is perfectly natural. After all, it’s logical that the most high-profile member of an organization should be at the heart of its PR efforts. It’s also true that the media is interested in speaking with decision-makers, which means founders and CEOs are sensible candidates.
However, the breadth of discussions that take place within the cyber-security industry – from security and compliance, to technology, to wider geopolitical issues – means it’s important for brands to provide varied, credible perspectives. Relying on one spokesperson alone for all press opportunities can bring about difficulties further down the line.
If journalists only ever hear from one individual, they can become reliant on that person and unwilling to hear from anyone else within the organization. After all, if they’ve enjoyed unchecked access to the CEO in the early stages of the organization’s development, why should they be persuaded to engage with anyone else?
Relying on a single spokesperson also neglects the depth of talent and expertise across any cyber-security business. Raising the profile of a variety of spokespeople from different areas of the business – technical, analytical, and high-level – allows a cyber-security brand to paint a more complete and coherent picture of the challenges it is seeking to address.
However, there’s one exception to this rule. Broadly, journalists don’t want to hear from sales people. No matter how articulate, charismatic or credible they might be, the title triggers a suspicion that’s difficult to move beyond.
The right tool for the job
As with anything, it’s important to use the right tool (or in this case, spokesperson) for the job. Each media engagement is different and should be treated as such when it comes to selecting the most appropriate spokesperson.
For example, a written comment for a security publication on a breach resulting from a system vulnerability would represent a great opportunity to utilize the expertise of a technical spokesperson. Not only is the head of research, for instance, more credible than the CEO in this scenario, but they’d also be capable of providing more specific insight into the issue.
On the other hand, if a tech publication is looking for a perspective on the human issues at the heart of the cyber-security industry, or insight into the broader direction of the business, then the CEO is the obvious choice.
It’s also important to consider the abilities and qualities of your spokespeople. For example, is the spokesperson comfortable in front of the camera or microphone? If not, might they be better suited to authoring a comment or article? Is the spokesperson’s passion for the product likely to cause problems in a situation that calls for a measured response? Is the spokesperson likely to get caught up in the technical detail?
Taking the time to think about questions such as these and ensure you use the right person for each specific situation can spell the difference between success and mediocrity.
In a nutshell
When it comes to building out a cyber-security spokesperson matrix and cultivating an authoritative brand voice, it’s vital to tap into the whole breadth of expertise within the organization, as opposed to relying on a single spokesperson to provide insight.
Take time to consider the strengths and limitations of each spokesperson, and the kinds of media each could most effectively engage with. When selecting which spokespeople to use for which media engagements, context is truly king.
Need help selecting your spokesperson bench, or delivering media training for spokespeople? We can help. Get in touch at hello@rlyl.com.
Do cyber-security brands need to maintain a serious tone of voice?
By Dan Simpson
There’s a belief within the cyber-security industry that, because information security is no laughing matter, brands’ tone of voice should always remain serious. But is it time for cyber-security marketing professionals to reject sincerity and embrace variety?
We think so. Given the current level of competition in this space, adopting a tone that’s markedly different from your competitors is a great way of cutting through the noise. Here are a few strategies to introduce variety and individuality to your cyber-security brand’s tone of voice.
Don’t be afraid to get emotive
The thought that b2b marketing can’t generate an emotional response is a myth. Emotions such as fear, uncertainty, risk, reassurance and trust are all at play in the b2b world – exploit them to drive a response from your prospects and customers.
You might have noticed that b2c marketers are great at doing this. Follow their lead to engage your target audience with a more entertaining, engaging, and emotional tone of voice.
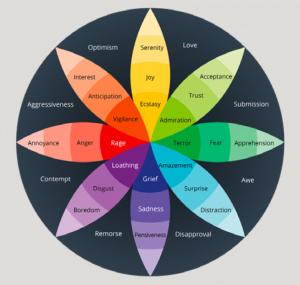
Plutchick’s model: source
Speak your prospects’ language
It’s important to remember that behind every purchasing decision is an individual, or set of individuals, that a cyber-security brand must reach. These decision-makers are people like any other!
One way to ensure your brand is accessible and relatable is to use colloquial and informal language in marketing materials and on social media. This way, you come across as genuine and approachable, rather than severe and robotic. Contrary to the popular belief, an informal tone doesn’t affect a cyber-security brand’s credibility.
It’s also vital to instill a genuine enthusiasm for the product in your employees. This belief and passion will communicate itself to anyone who interacts with a staff member, whether in-person or online. And make sure you’re encouraging employees to use social media. You’ll often find that messages from individuals resonate better than those that come from a corporation – even if you’re saying the same thing.
Make them laugh
Laughter is the best medicine…unless you’re diabetic, in which case insulin is pretty high on the list. We have Jasper Carrott to thank for that one!
Joking aside, humor has many benefits when it comes to cyber-security marketing. It can allow brands to:
- Engage and entertain
- Build trust with an audience
- Showcase their human side
Humor is a fantastic way to imbue a brand with personality. And yes, this includes memes. But it’s also important to remember that it doesn’t fit all occasions. For the greatest impact, humor is best used selectively!
Cut the jargon
The language of cyber-security is ever-evolving, and new industry jargon pops up with each passing week. However, from a PR and marketing perspective, the influx of technical language means that brands can struggle to communicate themselves to those who don’t operate within the cyber-security bubble.
Audiences’ varying knowledge means it’s crucial for cyber-security brands to adapt the language they use to the specific situation, and cut the jargon where necessary. Whilst a network engineer will understand the technical lingo, a CEO almost certainly will not. It’s equally important to cater to both individuals when considering your cyber-security marketing strategy, because both personas play an integral role in the decision-making process.
Honing in on the human impact of the product, rather than dwelling on its features or the technical specifics, is a great way to reach all stakeholders and audiences with a story that will resonate. Though not everyone understands the nitty gritty, all parties understand the significance of the right to data privacy and the potential consequences of a breach.
Why so serious?
So, there we have it! Though there’s certainly a time and place for sincerity, it’s important for cyber-security brands to introduce variety and personality to their marketing strategy in order to differentiate themselves from the competition.
Employing tactics such as using colloquial language, leaning on humor when appropriate, and avoiding jargon where possible can go a long way to establishing a unique and nuanced voice – something that all brands are striving for in today’s crowded cyber-security market.
Struggling to find quite the right tone for your cyber-security brand? We can help. Get in touch at hello@rlyl.com.
Landing a media briefing at cyber-security trade shows like Black Hat
Cyber-security conferences and trade shows offer a great opportunity for companies to meet with press and analysts face-to-face. But attracting their attention can be easier said than done. For starters, press and analysts have limited time to meet with vendors – especially since they’ll be interested in attending several sessions throughout the week. Companies are also competing for face time with dozens (if not hundreds) of other vendors. So, you’ll need to be able to offer something tantalizing to pique their interest.
Here are a few ideas to help secure yourself some briefings at any trade show or conference:
- Hands-on experiences: What can you offer in person that a reporter or analyst won’t be able to get over the phone? This could be anything from offering a live demo at your booth, a photo or video opportunity or an early look at a new product.
- Unveiling research: Have you uncovered a new ransomware trend? Or an additional step in the ever-changing customer journey? Technology trade shows are great for unveiling new research that highlights how the industry is evolving. If you’ve already got a research project in the budget for a different campaign, consider keeping a few findings under wraps that you can release later during an appropriate conference.
- Unleash your heavy hitters: Media will be more interested in speaking with one of your c-level spokespeople than, say, someone in marketing or sales. These are the changemakers within an organization, and have the authority to discuss broader trends and issues impacting the industry that media are writing about.
- Major news: Announcing news at a trade show can be risky. On the one hand, you have a captive audience. On the other, you won’t be the only one announcing news – far from it. The most successful news announcements at trade shows offer something truly new and exciting, whether it’s a new product or a complete overhaul of an old one. New customer or partnership announcements won’t carry as much weight – especially if that customer or partner isn’t attending the show with you, or the results of your partnership have yet to be realized.
- Keep your eyes on the prize: Media and analysts will likely be strolling the expo floor, so keep those eyes peeled for opportunities for a quick hello (without becoming a stalker!). Press and analysts are often given special passes that are clearly labeled, so take a look at who’s around you next time you’re in line for coffee or lunch (or simply walking by your booth). Exhibitors will also often get access to a list of attending press and analysts, so familiarize yourself with who will be in attendance, and select a few you want to look for specifically.
- Early bird gets the worm: Evenings are usually chock full of events and parties, but early mornings before the expo hall opens can be a prime opportunity to take a reporter or analyst out for breakfast or coffee before the day properly begins.
Don’t take our word for it
We asked some media friendlies for anonymous tips on what they look for when accepting briefings at trade shows. One is an editor at a top cyber-security trade publication. The other is an editor at a leading publication covering software-defined technologies :
I take meetings with folks who are working on new research or findings, or have expertize in an area that I am writing about.
A lot of it is based on the company and the exec being offered for an interview. About the company: is it one that readers care about and click on stories about? […] Have they been in the headlines recently for good or bad reasons? Do I think their technology is interesting and do I think readers should keep this company on their radar? If it’s a startup: are they doing something new and innovative that I want to learn more about and think readers should as well? I also look at the executive being offered for the interview; a CEO, CISO, CTO, etc. is much more appealing than a product marketing guy.
It’s not always about coverage
Not every trade show media briefing will result in coverage – and that’s fine! Briefings for the sake of relationship-building are a great way to let press and analysts get to know you and your company. Plus, they keep you front of mind next time they’re working on an article or report. Background briefings can also help establish trust and give media an opportunity to vet you as a potential future source.
Securing media briefings can be a time-consuming task – especially when timing is everything. Some media and analysts like to start planning their schedules three to four weeks in advance of a trade show. Others like to wait until the week before to fill their calendars.
Need some extra help with your cyber-security trade show prep? Drop us a line at hello@rlyl.com.